Best Ways to Avoid the “Heartbleed” Bug in OpenSSL and Skype and Secure Your Site’s User Data
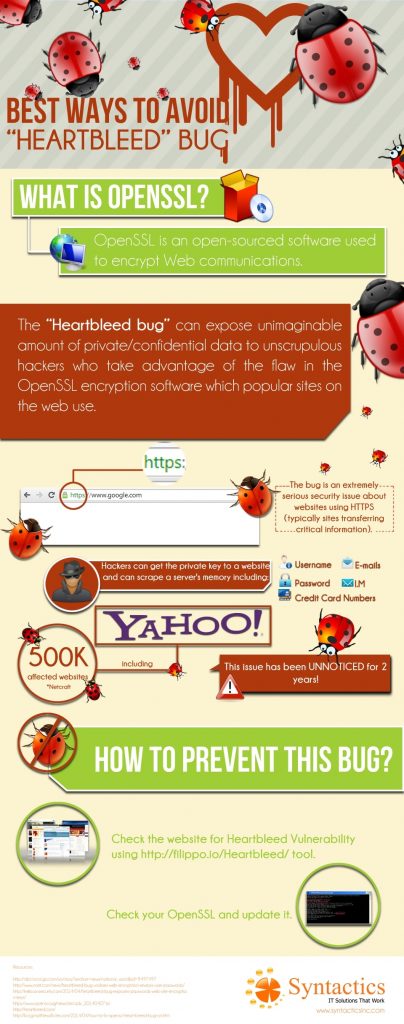
The “Heartbleed bug” is sending shockwaves on the Internet right now as it infiltrates systems using OpenSSL and threatening website security. This bug can expose unimaginable amount of private/confidential data to unscrupulous hackers who take advantage of the flaw in the OpenSSL encryption software which popular sites on the web use. Many project/dedicated developers and outsourced developers use OpenSSL to encrypt Web communications, and is an open-sourced software.
The Heartbleed bug is an extremely serious security issue about websites using HTTPS (typically sites transferring critical information). The scary truth about this is that hackers can get the private key to a website and can scrape a server’s memory including:
- usernames
- passwords
- emails
- instant messages (Skype, WhatsApp, etc.)
- credit card numbers, and other sensitive data stored in servers
In fact, according to Netcraft, an Internet research firm, 500,000 websites are affected by the Heartbleed bug including Yahoo.com, but what really shocked everyone is that this issue has been unnoticed for 2 years! Hackers could have been silently stealing sensitive information during that period.
While high-profile websites certainly know about the problem, small business websites might not even be aware of it. That is why it is imperative that you do what you can to prevent your site from being affected by the bug.
According to Syntactics Engineering Lead – Web Division, Mr. Djane Rey Mabelin, you need to:
1. Check the website for Heartbleed Bug Vulnerability using heartbleed by filippo tool.
This tool is published by Filippo Valsorda, developer and cryptography consultant. This is also the tool that made Google, Facebook, Dropbox, Microsoft, Twitter, and many other major websites unaffected. However, he said that caution is still advised even if the tool gives you an “all clear” or “unaffected” indication.
Mr. Mabelin also warns that Internet users must change their online profile accounts passwords to invalidate exposed information.
2. Check your OpenSSL and update it.
According to reports, version 1.0.1 and 1.0.2-beta releases of OpenSSL are vulnerable to Heartbleed bug. If you use such OpenSSL version, upgrade to the latest iteration of OpenSSL – OpenSSL 1.0.1g – as soon as possible.
Upgrade only the OpenSSL rather than upgrading everything on your server. Once finished, check the version again if you have successfully upgraded it. After that, generate your certificate using a new private key, then restart your Apache server and any services using SSL.
Those who are unable to immediately upgrade can alternatively re-compile OpenSSL with -DOPENSSL_NO_HEARTBEATS.
The devastating fact about the bug is that you cannot get back the data that hackers stole from your website. As Mr. Mabelin says, even if you upgrade your OpenSSL, the damage has already been done.
This might serve as a lesson to everyone to check their site’s vulnerability to avoid the Heartbleed bug and other bugs from time to time to avoid compromising security in all online transactions.
Have you already reformed your website security practices with your own dedicated developers? What do you think about the Heartbleed bug?












1 Comments